More Details about HTML: Defacement-V [Trj]
HTML: Defacement-V [Trj] is a malicious Trojan horse, which aims at corrupting the target computer and compromising users’ security on purpose. This Trojan horse will connect its servers to get instructions to active in the target computer. In this case, this Trojan horse will open a backdoor through system loopholes to allow the remote hackers to get into the target computer and steal your information.
After executing, HTML: Defacement-V [Trj] would change your system files and registry entries to make your system vulnerable for other harmful attacks like spyware and ransomware. It can also modify your essential system settings and erasing vital files at random. The running of this Trojan needs a great amount of system resources, so it would degrade the system performance and messes up your files terribly. That is why some of your programs cannot run smoothly and often get some pop up alerts, and you will find some of your files are missing and some unfamiliar files get into the computer without your awareness.
And worst of all, HTML: Defacement-V [Trj] has the ability to monitor your online activities and record your browser history without consent or permission. Then it will send your credit card numbers, logon names, passwords, online banking information and other valuable information stored on the computer to the remote severs in order to obtain illegal profits.
The following passage is going to offer TWO useful instructions on removing HTML: Defacement-V [Trj] for you. Free to choose the one you prefer to help you to fix the issue.
- Option One: HTML: Defacement-V [Trj] Manual Removal Instruction
- Option Two: HTML: Defacement-V [Trj] Automatic Removal Instruction Using SpyHunter
Option One: HTML: Defacement-V [Trj] Manual Removal Instruction
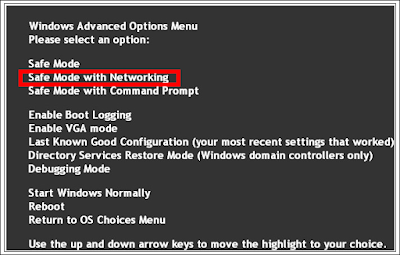
Step 1. Restart the computer and put it in Safe mode with Networking
Restart the computer and start hitting F8 key repeatedly when PC is booting up again; if successfully, Safe mode options will show up on the screen for you to select. Please use arrow keys to highlight Safe mode with Networking option and hit enter key. System will be loading files into this mode afterward.
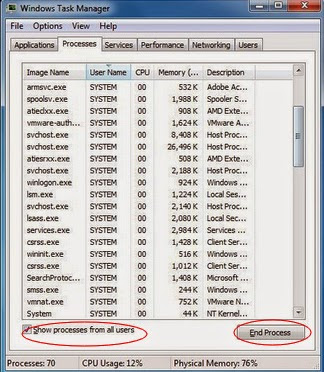
Step 2. End all the harmful running processes
Open task manager by pressing Alt+Ctrl+Del keys at the same time. Another way is to click on the Start button and choose Run option, then type taskmgr into and press OK. Stop all the suspicious running processes.
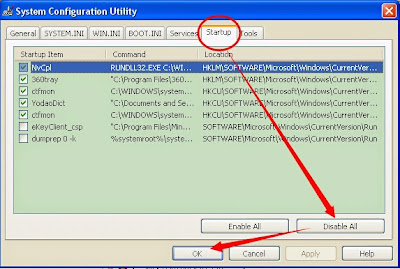
Step 3. Disable any suspicious startup items that are made by HTML: Defacement-V [Trj]
Click Start menu; click Run; type: msconfig in the Run box; click OK to open the System Configuration Utility; Disable all possible startup items generated.
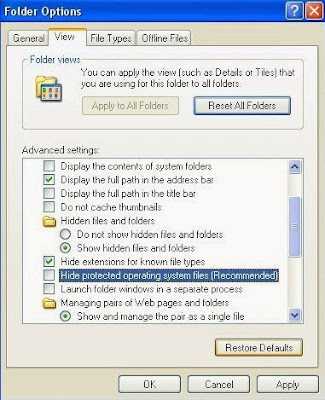
Step 5. Show hidden files and folders and delete all the following files.
Guide: click the Start button and choose Control Panel, clicking Appearance and Personalization, to find Folder Options then double-click on it. In the pop-up dialog box, click the View tab and uncheck Hide protected operating system files (Recommended).
Step 6. Remove all the malicious registry entries as follows:
Open Registry Editor to delete all the registries as below Guide: open Registry Editor by pressing Window+R keys together.(another way is clicking on the Start button and choosing Run option, then typing into Regedit and pressing Enter.)
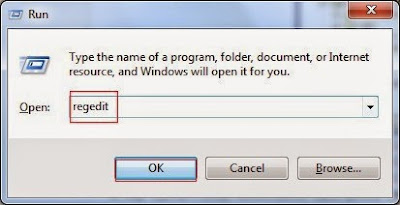
Delete all the vicious registries as below:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\MSASCui.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msconfig.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msmpeng.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msseces.exe
HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Winlogon "Shell" = "%AppData%\.exe"
HKLM\SOFTWARE\Classes\AppID\.exe
There may be some other issues such as windows registry errors in your system. To avoid potential risk and to ensure your computer security, you are suggested to use RegCure Pro to optimize your system after the threat removal.
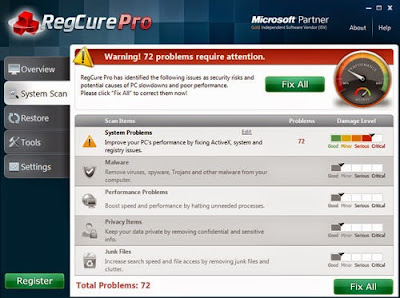
Step 7. Optimize your PC using RegCure Pro
What can RegCure Pro do for you?
- Fix system errors
- Remove malware
- Improve startup
- Defrag memory
- Clean up your PC
1. Click the below button to download RegCure Pro to your PC.
2. Click the Yes button to enter in installation process and then follow the instruction to install the program step by step.
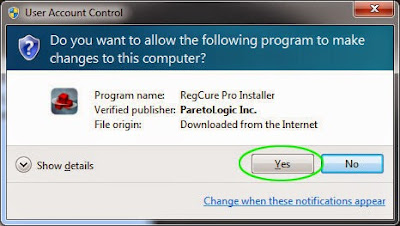
3. When the program is successfully installed, double click on its desktop shortcut to open it. On the Overview tab, check all the scan settings and then click on the Click to Start Scan button to run a system scan on your computer.

4. The first system scan will take some time, please be patient. The screenshot of the system scan progress is shown below.

5. When the system scan is done, click on Fix All button to completely remove all the performance problems in your computer.
>> Click Here to Download RegCure Pro to Fix Slow PC Performance! <<
Option Two: HTML: Defacement-V [Trj] Automatic Removal Instruction Using SpyHunter
What can SpyHunter do for you?
- Give your PC intuitive real-time protection.
- Detect, remove and block spyware, rootkits, adware, keyloggers, cookies, trojans, worms and other types of malware.
- Spyware HelpDesk generates free custom malware fixes specific to your PC
- Allow you to restore backed up objects.
Step 1. Click on the below button to free download SpyHunter on your PC.
Step 2. Click the Run button to enter the setup program and follow the installation steps until setup is complete.
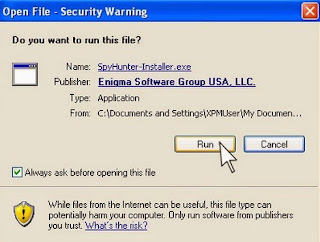
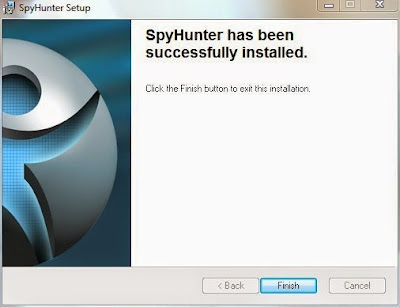
Step 3. When the installation is complete, click the Finish button to exit the installation.


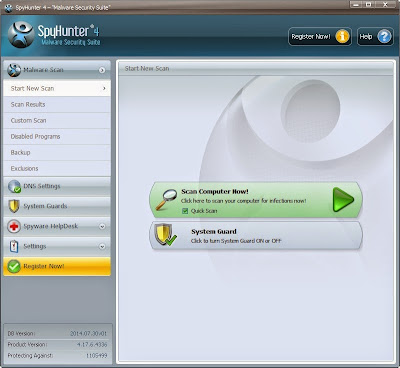
Step 5. Allow the program to scan by clicking the Scan Computer Now! button. If you would like to have a quick scan on your PC, please check the Quick Scan box; otherwise, uncheck it.
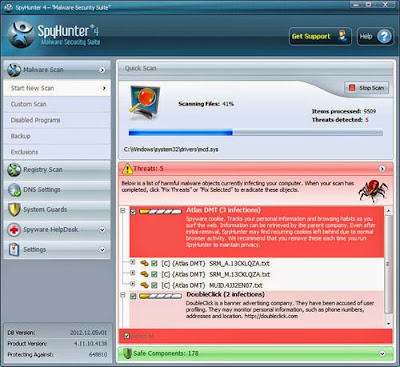
Step 6. The first scan will take some time, please be patient while waiting for the scanning result.
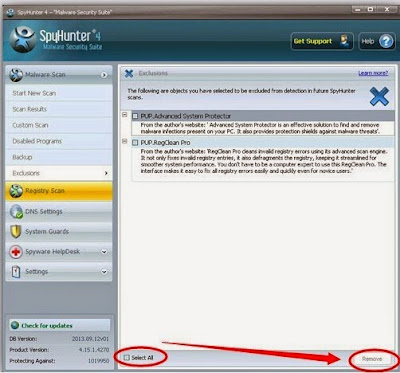
>>Click Here to Download SpyHunter to Try All the Features!<<


No comments:
Post a Comment